Flipper Zero Multi-Tool and Firmware Overview

At its core, Flipper Zero is a pocket-sized pentesting gadget that can scan, copy, clone and emulate wireless signals. With its firmware constantly evolving, the device has become a cult favorite among hacker communities and cyber security testers. It began as a Kickstarter project in 2020, raising $4.8 million, and since then has gone viral on TikTok. Videos show people using it to remotely control weather stations, prank retail employees, open Tesla charge ports, or unlock infrared remotes for TVs and air conditioners. Alongside the jokes, however, are more controversial hacks: bypassing access control systems, cloning hotel RFID cards, or experimenting with NFC and Bluetooth modules.
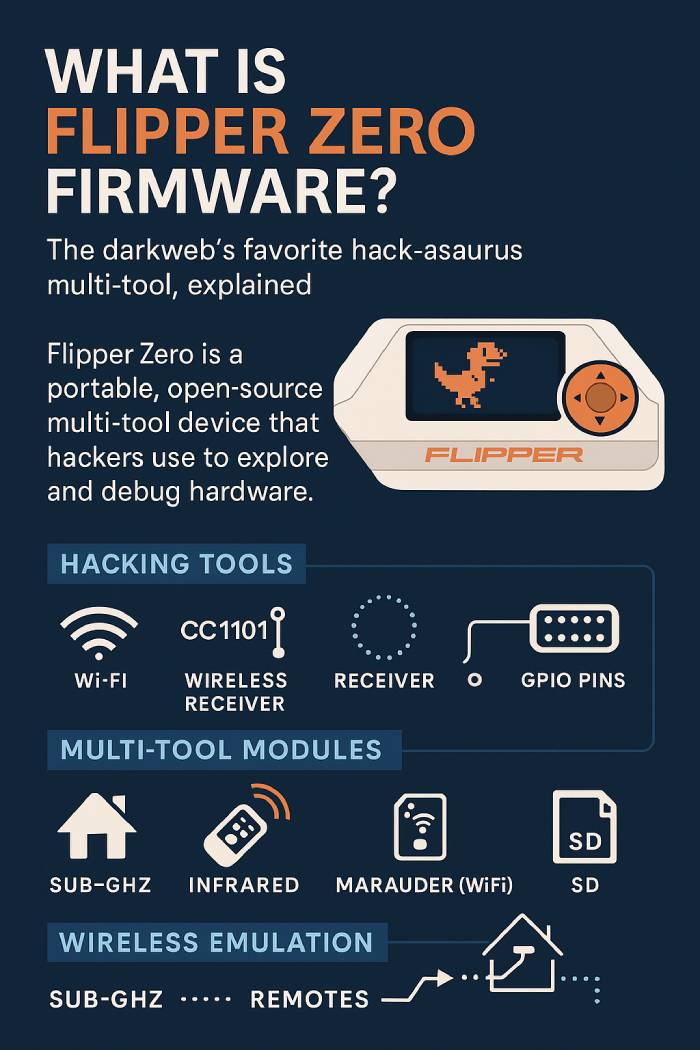
Flipper Zero Hardware, GPIO Pins and Modules
Flipper Zero is a portable, open-source multi-tool built on low-power hardware. It features an LCD screen, a D-pad, a transceiver, multiple radio protocols, and sensors packed onto its compact PCB design. The gadget is fully open-source and customizable, meaning its firmware, schematics, and modules can be tweaked by the community. Users can load Flipper Zero firmware mods to expand features like WiFi Marauder scanning, BLE (Bluetooth Low Energy) experiments, or even SDR-like signal analysis through the CC1101 antenna receiver and transmitter.
Inside, the device combines an MCU, GPIO pins, USB port, microsd card slot, and connectors for iButton, 1-Wire, SPI, UART, I2C, and debug interfaces. This makes it more than just a toy: it’s a serious piece of hardware for reverse engineering, cryptographic testing, and prototyping.
Gamification adds to the fun. The toy dolphin pet on screen reacts to activity, rewarding pentesting tasks like scanning NFC module tags, testing 125 kHz RFID module cards, or probing GPIO pin circuits. It’s hardware learning disguised as play.
How Flipper Zero Hack and Emulation Work
Flipper Zero acts as a transceiver and multi-tool device, communicating through different wireless protocols and emulating common remotes. The firmware interprets signals so the gadget can transmit signals, emulate cards, and interact with IoT systems.
It supports:
- SubGHz (low-frequency and high-frequency bands with modulation options)
- 125 kHz RFID module (LF) for badges, keyless systems, and animal chips
- NFC module at 13.56 MHz for contactless cards and payments
- IR (infrared) transmitter and receiver for remote control of TVs, AC units, and other digital stuff
- GPIO pins for sensors, relays, and testing PCB design circuits
- iButton (1-Wire) access keys
- BadUSB (Ducky scripts) for Windows computers and USB hacking tools
- BLE and WiFi Marauder modules for scanning and pentesting wireless environments
Because it can emulate remotes, clone RFID tags, or unlock infrared devices, security experts stress that Flipper Zero is as much a hacking tool as it is a tester. Yet it is compatible with Flipper Zero firmware extensions that expand safe, educational uses.
Flipper Zero in Numbers, IoT Security and Wireless Stats (2025 Update)
- In 2022, sales hit $25 million; in 2023, revenue jumped to $80 million.
- By 2025, more than 1 million Flipper Zero multitools have shipped worldwide, with a growing aftermarket for accessories like antennas and custom PCBs.
- Analysts note cyber security incidents in 2025 average 5,000 IoT-related attacks monthly, while more than 7 million records are compromised daily—numbers that fuel interest in DIY hacking tools and pentesting gadgets.
What Can Flipper Zero Multi-Tool Device Do?
Pentesting
With its modules and GPIO pins, Flipper Zero lets ethical hackers simulate attacks on access control systems, NFC module tags, or wireless protocols to identify weaknesses before criminals do.
Device Emulation
The firmware allows Flipper Zero to emulate remotes, clone RFID keys, unlock infrared devices, and transmit signals like a universal remote control. It can also interact with BLE and WiFi environments through add-on modules.
Script Automation
Seen as a USB HID tester, it can inject Ducky scripts into Windows computers. Plugged into USB, it can automate tasks, open backdoors, or perform debug operations.
Hardware Interfacing
With GPIO pin headers, UART, I2C, and SPI support, it connects to pcbs, sensors, and actuators. This makes it handy for schematic testing, pcb design prototypes, or experimenting with 5V digital circuits.
Flipper Zero Legal or Darkweb Risk?
Flipper Zero is legal hardware. But, like any hacking tools, its use determines the outcome. Bans in Brazil, restrictions in Canada, and Amazon’s “card skimming” label highlight the concerns. Yet experts remind us: more advanced testers already exist on the darkweb, from software exploits to custom transceivers.
Because Flipper Zero is fully open-source and customizable, it empowers the cyber security community to responsibly study wireless protocols, debug IoT systems, and test keyless entry devices. As consultant Michael Hasse put it: if regulators want real safety, they should demand stronger standards for wireless systems instead of singling out one multi-tool device.
Flipper Zero’s legacy may be less about pranks and more about inspiring a new wave of pentesters, hardware hackers, and curious tinkerers who push the boundaries of what’s possible with open-source firmware, low-power modules, and creative reverse engineering.

