Zero-Knowledge Proofs (ZKPs): Future Cryptography That Preserves Privacy
A revolutionary development in cryptography, zero-knowledge proofs (ZKPs) allow one party (the prover) to persuade another party (the verifier) that a particular assertion is true without disclosing the underlying information or the methodology used to arrive at the proof. This special capacity to demonstrate to another person that a claim is accurate without disclosing private information has wide-ranging effects on blockchain, authentication, and security and privacy applications.
The Zero-Knowledge Proofs Concept
Shafi Goldwasser, Silvio Micali, and Charles Rackoff's groundbreaking 1985 paper "The Knowledge Complexity of Interactive Proof-Systems" introduced the idea of zero-knowledge proofs. The foundational structure of ZKPs was defined in this paper, which also proposed a proof system in which a prover can persuade a verifier of a statement's validity without revealing anything more than the validity itself. Completeness, soundness, and zero-knowledge are the essential elements.
The amount of information that needs to be shared in order to establish a fact is known as the knowledge complexity of interactive proof systems. Reducing this complexity is essential as technology develops. The idea is particularly crucial when creating protocols that demand high proof fidelity with little interaction.
The Operation of Zero-Knowledge Proof
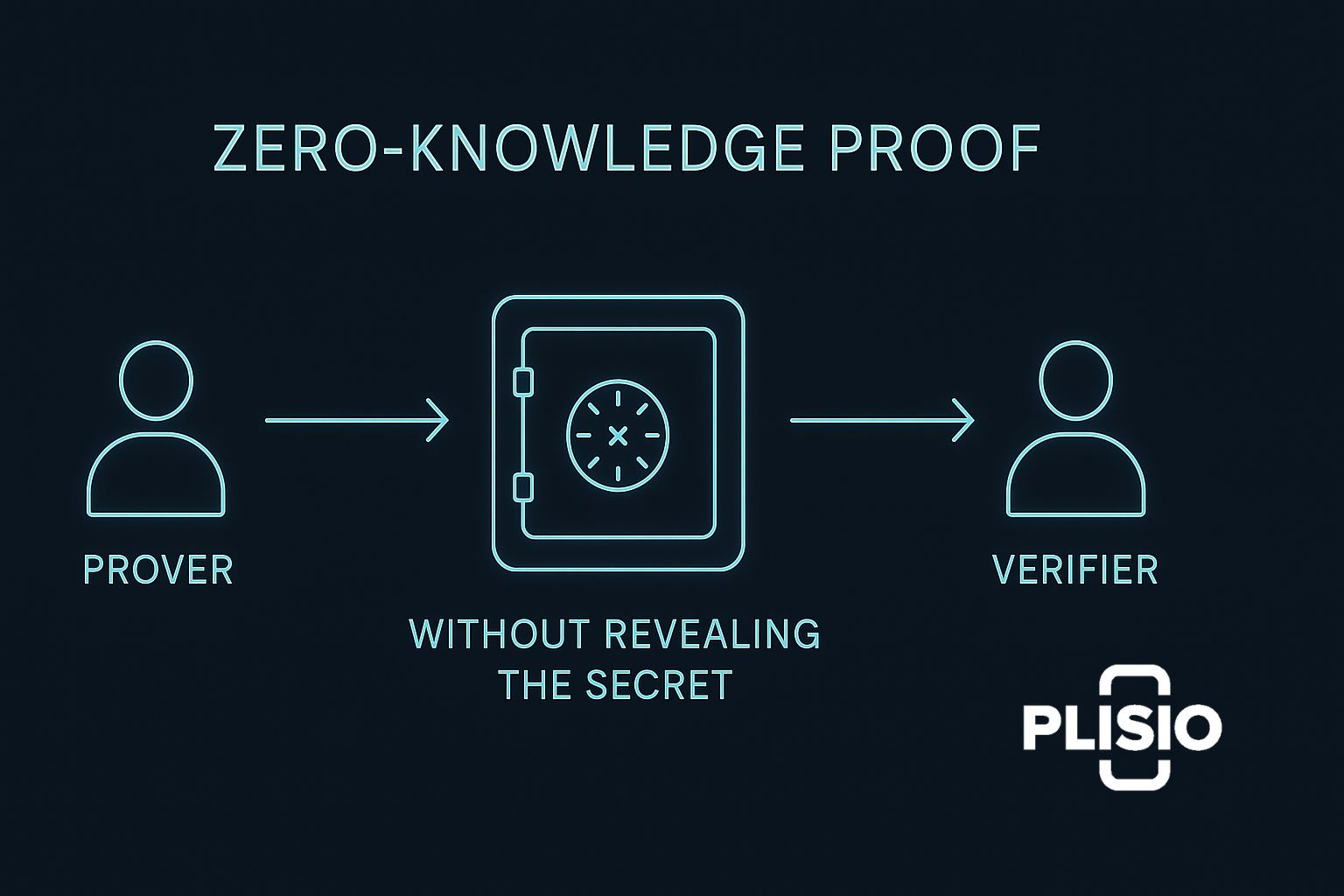
An example of a zero-knowledge proof can be useful in elucidating zero-knowledge protocols. Let's say Alice wishes to demonstrate that she is aware of a system's password without disclosing it. She can create a cryptographic proof that persuades the verifier that she is aware of the secret using a zero-knowledge protocol without disclosing the underlying information.
ZKPs come in two primary varieties:
- Interactive zero-knowledge proofs involve a back-and-forth conversation between the prover and verifier.
- Zero-knowledge proofs that are not interactive, in which the prover only transmits one message.
More scalable, non-interactive zero-knowledge (NIZK) models are frequently employed in contemporary applications, especially in blockchain technology.
Theory to Blockchain
Since cryptocurrencies like Zcash use zk-snarks (zero-knowledge succinct non-interactive arguments of knowledge) to protect transaction privacy, ZKPs have become essential to blockchain systems. Users can confirm the legitimacy of a transaction using these brief, non-interactive zero-knowledge proofs without disclosing any transactional information.
Zkp technology provides improved data privacy and authentication within blockchain and public blockchain networks, enabling parties to securely engage with public blockchain infrastructures. ZKPs are perfect for supply chain systems and multi-party computation because they allow one to validate a transaction or data point without disclosing its content.
ZKP usage is growing quickly in Web3 ecosystems, DeFi, and decentralized applications (dApps). They make it possible to use zero trust security models without the need for outside validation.
Uses and Executions
Among the many uses for ZKPs are:
- Verification of identity without revealing personal information
- Ensuring privacy through private blockchain transactions
- Elliptical curves are used in cryptographic proof to produce safe signatures.
- Compliance without disclosing private information
Among the more sophisticated frameworks are zk-snarks, which are designed for quick and concise verification, and bulletproofs, which are effective for range proofs. Other constructs that emphasize minimal assumptions, like a trusted setup, include the transparent argument of knowledge and the concise non-interactive argument of knowledge.
|
ZKP Type |
Interaction |
Trusted Setup |
Application Area |
|
zk-SNARKs |
Non-Interactive |
Yes |
Private Transactions |
|
zk-STARKs |
Non-Interactive |
No |
Scalable Blockchain Apps |
|
Bulletproofs |
Non-Interactive |
No |
Confidential Range Proofs |
|
Interactive ZKPs |
Interactive |
No |
Theoretical Foundations |
Foundations of Theory
Zk-snarks and other non-interactive knowledge systems argue that they need a trusted setup, which can be a weakness. This is the goal of succinct non-interactive arguments of knowledge (SNARKs) and their more recent variation, scalable transparent arguments of knowledge (STARKs). Not to be overlooked are bulletproofs, which are more secure in some situations because they don't need a trusted setup.
The Workings of ZKPs
Cryptographic complexity is necessary to comprehend zero-knowledge proofs. These cryptographic proofs, which are frequently based on elliptical curves, provide completeness, which guarantees that a valid claim can always be proven, and soundness, which guarantees that a false claim cannot be proven.
The prover creates a proof that the statement is true in a standard protocol. The verifier then uses verification mechanisms to confirm this proof. Advanced algorithms and an awareness of the knowledge complexity of interactive systems are necessary for such proofs.
Zero-knowledge is defined as the capacity to persuade a verifier without disclosing any additional information. For instance, one of the main characteristics of decentralized finance (DeFi) is proof without knowledge leakage. ZKPs serve as the cornerstone for creating zero trust environments in this sense.

Advantages and Difficulties
There are numerous important advantages to implementing ZKPs:
- Data privacy: Preserves user information while it is being transmitted and validated.
- Scalability: particularly in blockchains with SNARKs and STARKs
- Minimizing trust: Lessens dependence on centralized authorities
Nevertheless, difficulties include:
- Certain systems require a trusted setup.
- Overhead in computation when creating proofs
- Knowledge of secure integration among developers and educators
ZKPs are perfect for use in zero-knowledge proofs of knowledge, in which facts are confirmed while private information is exchanged between the prover and verifier. It is revolutionary to provide proof without revealing the data itself in extremely sensitive applications like healthcare or finance.
Gazing Ahead
ZKPs are essential to next-generation protocols as cryptographic techniques advance. ZKPs are intended to be used in new ways by developers, like delivering data points without disclosing context or guaranteeing verifiable computation across decentralized nodes.
As ZKP applications become more specialized and sophisticated, new research investigates lagrange-bases for oecumenical and oecumenical noninteractive arguments of knowledge. Organizations seek to improve security and scalability as they implement zero-knowledge proofs of knowledge.
ZKPs are the foundation of contemporary privacy-preserving technologies, to sum up. Adopting ZKP-based systems requires the following actions:
- Consider the use case and the sensitivity of the data.
- Select the proper ZKP framework (such as bulletproofs or zk-snarks).
- Include the ZKP in the larger blockchain or cryptographic system.
The field keeps expanding, enabling prover-verifier interactions in a privacy-conscious world, thanks to pioneers like Silvio Micali and Shafi Goldwasser.
To sum up, ZKPs make it possible for private, secure online interactions. ZKPs offer a vital tool in contemporary cryptography, whether it is for identity verification, blockchain data protection, or private computation. ZKPs will be essential in creating safe digital futures as adoption grows throughout blockchains and cryptocurrencies.